Commvault Unveils Clumio Backtrack - Near Instant Dataset Recovery in S3
Provisioning Users Automatically in Clumio
Integration Speeds Communication
We all live in a highly dynamic world where people from different backgrounds come together and work as a team to achieve great success for themselves and their organizations. When we all speak similar languages, it is straightforward for us to communicate with each other. In the technology world, there are multiple different companies building products using their languages to achieve their product objectives.
Oftentimes, these companies do not integrate easily and might require developers to spend months, if not years, to bring their products together. This is where standards and protocols are important to ensure that products across different organizations can all speak the same language.
Ubiquitous SSO and Active Directory
Let’s take a look at Single Sign On (SSO). This is an established standard that allows users to authenticate with one service, providing them access to several different applications inside their organization. In the morning, once you log into Okta, you don’t need to keep logging in again and again into tens (if not hundreds) of applications throughout the day. This access is provided to you by your central IT team to ensure a seamless, barrier-free user experience. Clumio added support for SSO in April 2020.
While SSO solves the user authentication challenge, user provisioning is still a bit difficult. It already has a System for Cross Identity Management (SCIM) standard, but many vendors are still behind in adopting it. Instead, they use a workaround that allows users to be provisioned automatically or just in time. In keeping with our mission to simplify user experiences, Clumio has added support for automatic user provisioning via the user’s association with Active Directory Groups.
This allows users to easily access the Clumio portal if they belong to an allowed directory group and have the corresponding application assigned in their Identity Portal such as Okta. Clumio takes it one step further by allowing users contextual access to ensure they get appropriate Roles and Organizational Unit access. More details about these features can be found here. Let me show you how it’s done in the product.
Easily Configure User Provisioning in Clumio
Go to Settings – Access Management – Auto User Provisioning
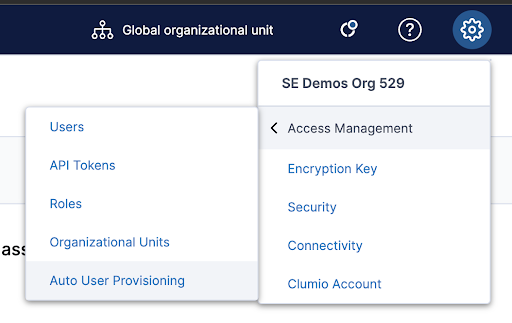
Customers then configure Auto Provisioning Rules to decide what Active Directory Groups get access to the Clumio portal. The rule also allows customers to determine what Role and Organization Unit the user gets once they get access to the Clumio portal.
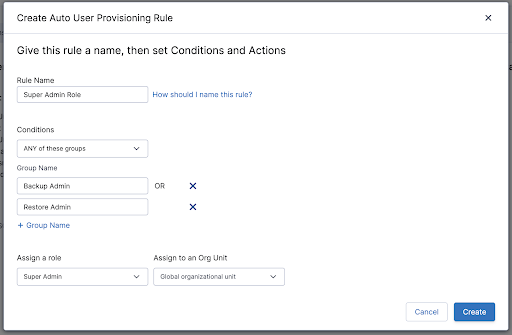
You can configure several different rules to ensure that users within your organization are only able to access data under their responsibility inside the Clumio portal.
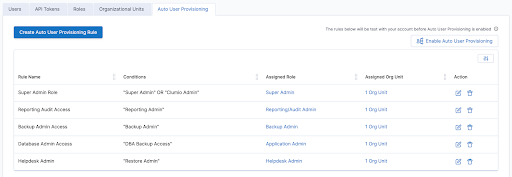
Once all the rules are configured, customers can Enable Auto User Provisioning and ensure that all administrators inside Clumio get access as per their Active Directory Group attributes.
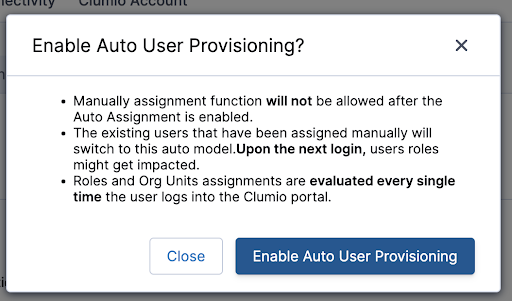
We have several different customers starting their administrators with the Read-Only role so that they cannot damage configurations while they ramp up, eventually, allowing them more accessible by adding them to another AD Group. This ensures that the user experience remains unchanged in terms of accessing the Clumio portal while allowing a safe onboarding to lead to greater access.
Clumio protects users from lockout
While user provisioning is extremely powerful, it can also be possible for users to lock themselves out by configuring something that removes their access and doesn’t allow them to modify anything in the future.
We built no-lockout functionality into our platform from the beginning, so users can be assured that Clumio has their back!
Highly secure configurations
Cybercriminals have become wise to the fact that would-be victims are backing up their data, and are responding by targeting those backups for deletion. With Clumio, since all the backups are immutable and there’s no delete button, even if a hacker did access your Clumio account, there’s no way for them to delete your data!
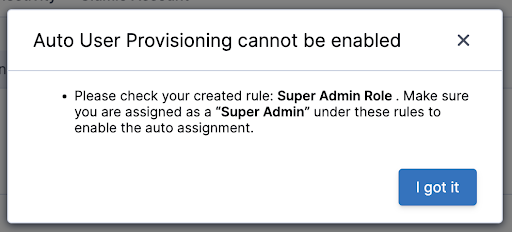
With the User Auto Provisioning feature, customers can take their security stance even further to ensure that no administrator has a Super Admin role within Clumio. When the customer first configures the rules, they can assign Administrators an AD Group that gives those Administrators Super Admin access.
Once all the rules are set up, customers can remove all Administrators from that AD Group. In the future, if any administrator needs access to the Super Admin role, then they will need to have this AD group assigned to them by their administrator.
Closing remarks
No one likes managing an additional application and while the configuration and management might be easy, it does add up. If these applications can do anything to make the lives of their customers easier, then they should take that extra step in doing so!
Being able to talk the same technical language across vendors at least ensures that administrators of these applications do not need to learn something new and bring their existing knowledge to the new application.
