Commvault Unveils Clumio Backtrack - Near Instant Dataset Recovery in S3
RBAC vs EBAC for Data Compliance: Clumio Insights
Today, as Enterprise Administrative teams are being asked to do more with less, the push for self-service has never been greater. Off-loading mundane tasks like user requested backups and file restores frees up time on the Core IT team to focus on more mission critical tasks. However, granting access to these powerful tools which house your company’s most critical data should be tightly controlled in order to meet data compliance needs and prevent any unintentional or malicious consequences.
So how do you give access to users to perform these valid functions but prevent any unintended or harmful consequences? Simple, a combination of RBAC and EBAC enables you to provide user access that conforms to your organization’s data compliance requirements.
What is RBAC and How to Use it?
Role Based Access Control or RBAC has been around forever, and administrators are very familiar with the concept. At its simplest form specific users can be given Read-Only, Write, or Read/Write access. In the old days of simple file shares, this satisfied most people’s needs. However, in today’s enterprise world we need much more fine tuned granularity.
The days of giving full Super Admin to everyone are long gone. Only a select few users should have this God-level permission and it should be highly monitored and audited. On the flip side, read-only can be too restrictive and can prevent users from doing what they need to do, causing them to open tickets with the IT Team. A happy middle ground must be possible.
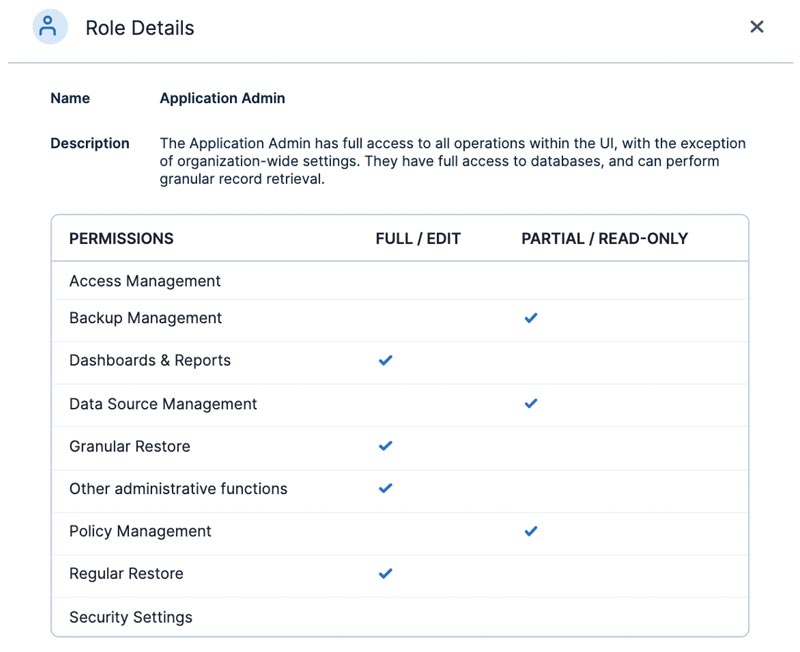
At Clumio, we give administrators the ability to give their end-users specific predefined roles that would more closely align with their job function without being too open or restrictive. At a glance, the below list of roles should fit 99% of permission levels administrators wish to give their users without “giving away the keys to the castle.”

Additionally, each Role has fine grain controls.
What is EBAC and How to Use it
Entity Based Access Control or EBAC is a slightly newer concept that allows you to put guardrails around specific resources and group them together to further control what your users have access to. This concept works great with Enterprises and even MSPs (Managed Services Providers) as it allows better support to enable more of a self-service experience for basic user requests.
Clumio’s approach to EBAC introduces the concept of an Organizational Unit or OU. Administrators can create these OUs and then place specific users and resources inside of these OUs to create isolation, restrict outside access, and reduce the blast radius in the event of unauthorized access. Let’s take a real world example to demonstrate how RBAC and EBAC function together to deliver a simple yet powerful mechanism to manage data access.
How RBAC and EBAC Work in Cohesion
In the below diagram we have created 3 different OUs – AWS Team, VMC Team and M365 Team. Inside each of these OUs are specific resources such as AWS accounts, VMware Cloud on AWS SDDC’s, and M365 Domains.
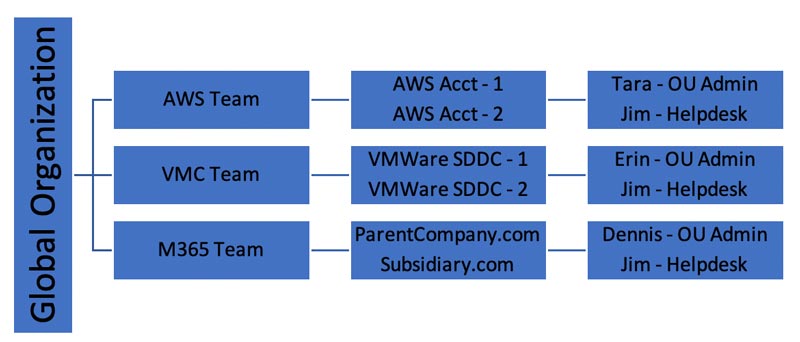
For example: When the user Dennis logs in, he can only see resources in the OU that he belongs to which are the two M365 domains. Dennis is an OU admin so he has full control over everything inside his M365 Team OU, but he has no access or visibility into the VMC Team or AWS Team’s OUs.
On the other hand, Jim is on the Helpdesk and his user account exists in all three OUs. When Jim logs in, he has visibility to resources inside all three OUs, but his restricted helpdesk permissions only allow him to perform specific functions within each of the OUs of which he is a member.
In summary, RBAC controls what you can do and EBAC controls what you can see. By combining these two control methods, you can safely grant access to powerful enterprise tools such as Clumio and conform to your data compliance needs.
Check out this demo to see how you can quickly set access controls in Clumio.

