Commvault Unveils Clumio Backtrack - Near Instant Dataset Recovery in S3
Enhancing Clumio’s Bring Your Own Key (BYOK) Feature
Don’t you love the beginning of the year when you come up with a resolution that gives a surge of motivation to achieve? But as new priorities emerge, your determined sprint inevitably becomes a leisurely walk. So long as you periodically remind yourself why you made the resolution in the first place, even slow progress will eventually get you to your goal.
That sense of accomplishment accompanies an added sense of relief, regardless of how long it took to achieve. But…what does this have to do with Bring Your Own Key (BYOK)? Read on.
Along similar lines, Clumio’s Backup as a Service Cloud promised to support the BYOK feature more than 2 years ago! This feature allowed customers to encrypt their backup data using their own encryption key using the Amazon Web Service (AWS) native Key Management Service (KMS) feature.
AWS KMS makes it easy for customers to create and manage cryptographic keys and control their use across a wide range of AWS services and in their applications.
When Clumio added the BYOK feature, it supported VMWare, Microsoft 365 (M365) and AWS EC2/EBS data sources as these were the data sources Clumio supported at that time. However, between then and now, Clumio added additional critical data sources like S3, RDS and DynamoDB.
Now with the most recent release, Clumio has brought BYOK capabilities to all of our critical data sources, and in doing so has achieved the resolution we started long ago. And it doesn’t stop here, as we will continue to invest efforts to bring BYOK to future data sources also.
Why do customers care about BYOK:
Doesn’t Clumio encrypt all backups already, and if yes, why is BYOK needed? It’s true that Clumio does encrypt all the backup data in its cloud with a customer-dedicated key, and that key is also rotated every 30 days. However, in some cases, certain customers have additional stringent security requirements:
-
These customers have to ensure that their own customers’ data is encrypted using that customer’s own key
-
These customers want to ensure that they can readily revoke access to the backup data whenever needed.
-
These customers want to ensure that they can audit every time their data is accessed along with the reason why it is being accessed.
-
These customers want to enhance their Zero Trust security posture by ensuring that even if Clumio is compromised, attackers cannot access their data
How encryption works:
AWS S3 bucket keys have reduced the cost of server side encryption by more than 99% and don’t need to lookup the key for every single transaction. Since Clumio backs up data with millions of transactions, having to look up the key for every single transaction was a no-go. With AWS’S S3 bucket keys feature, Clumio can use the customers BYOK key as the Amazon S3 Bucket Key and encrypts all the data landing in the S3 bucket using the customers BYOK key.
How To Enable the BYOK feature:
Go to Settings and Security Features – Encryption Key. When you go to the page, Clumio provides details about the feature, along with its requirements and limitations. Customers can proceed by deploying the AWS CloudFormation StackSets inside any one of their AWS accounts where they want to use the BYOK key.
The reason StackSets is needed is because Clumio will need to create a multi-region (global) key and use that for encrypting backups in all regions where the data sources are present. Once successfully deployed, customers can verify the connection in the Clumio UI by visiting the page at any time.
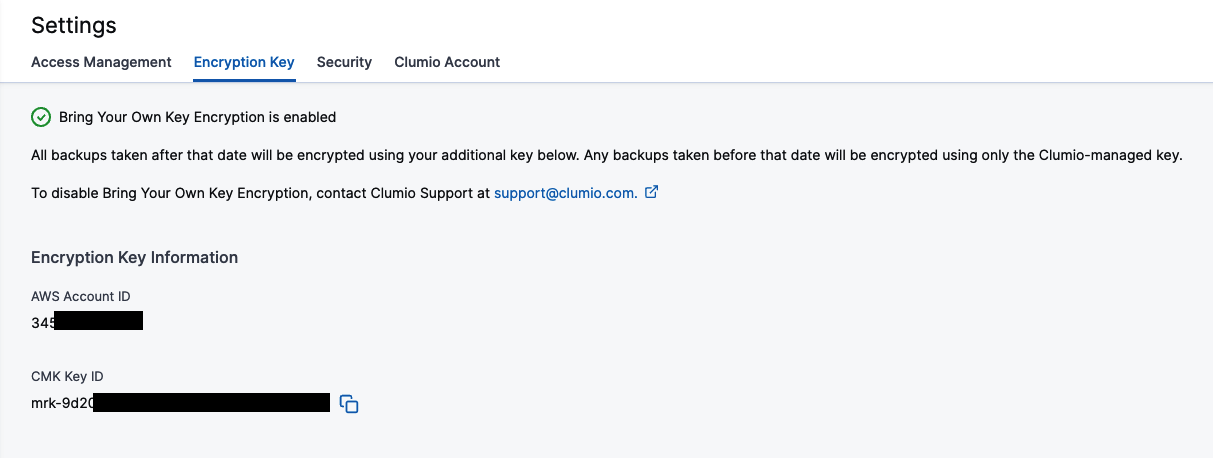
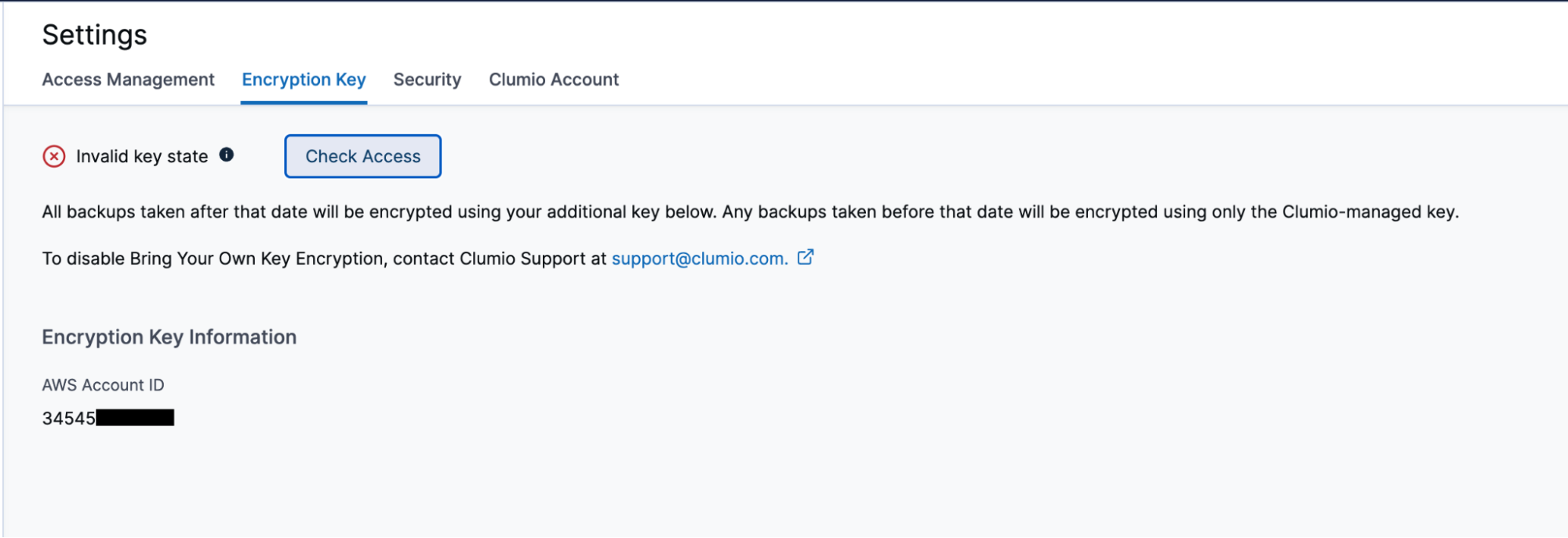
The green check at the top of the page indicates that everything is working as expected. For whatever reason, if the key is not accessible, it changes to a red X and allows you to Check Access again to see if things are resolved and working again.
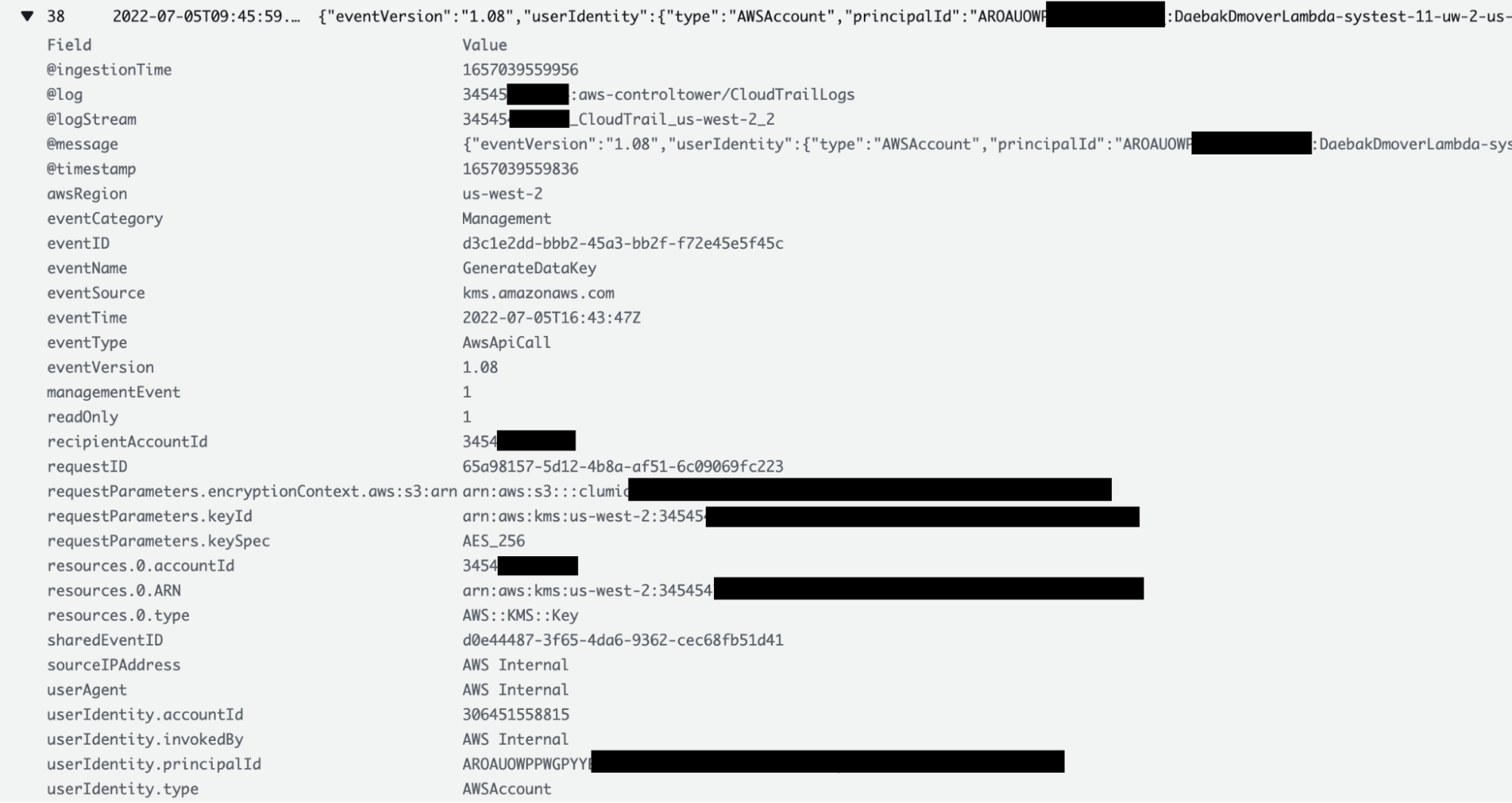
How to verify and audit Clumio’s Access
One of the advantages of the BYOK feature is that customers can verify and audit any time Clumio has accessed their key. Customers can go to the CloudTrail logs and see all the details of each time Clumio accesses their key, including the reason for access. Customers can go to the CloudTrail Logs section in their AWS account where the AWS CloudFormation StackSet was deployed.
For S3 bucket keys, since the keys are cached by the AWS S3 bucket keys, access might not be present for every single transaction. However, keys are accessed for every single transaction for EC2/EBS, VMWare and M365 backups.
What happens when key is no longer accessible:

Remember this: BYOK gives you the power of encrypting all backup data, but on the flip side, if the key is lost, then you’re in big trouble! Luckily, keys in AWS aren’t like physical keys and even if someone deletes them, customers still get 30 days to recover them. For whatever reason, if the keys are not recovered, then backup data would be rendered useless. It is meant to be used as a fail safe mechanism but great care should be taken to use this feature.
