Commvault Unveils Clumio Backtrack - Near Instant Dataset Recovery in S3
Get Greater Backup Insight with Clumio’s Splunk App
Exciting news today for all of you Splunk fans out there in Clumio Nation. Our new Clumio Splunk App is now generally available and live on Splunkbase! With this Clumio app, we are completing the story that was started with the launch of Clumio Audit Logs Ingester Add-on back in October. Our new Splunk App provides greater insight and visibility into Clumio’s audit logs. This is just the start of our plans to provide you with greater insights into your cloud environments. The Clumio App for Splunk delivers insightful and comprehensive views and analysis with drill-down capabilities. We are excited to have you give the app a try and look forward to your feedback.
Let’s dive into more of the specifics for the app below:
First you want to make sure that you have downloaded and installed our Splunk add-on “Clumio Audit Logs Ingester.” This tool brings Clumio’s audit logs into Splunk, in near real-time, and must first be installed and configured for our new Splunk app to work its magic. We have written before about how audit logs are like security cameras and are required to capture the events happening in your enterprise environment. I provide a full breakdown of the configuration for Clumio Audit Logs Ingester here
Top 3 Interesting Search views on the Clumio App:
1: Failed logins time chart
This view will provide the failed logins in a timeline chart. The Backup administrator must be able to get a record of all unsuccessful logins to my Clumio Org so that it can meet my security auditor’s requirements. The full login record contains details of the login time, source IP address, and email address. If you see a spike in login failures, then you know something is wrong and with a possibility of hacking. This view has a time-based filter to narrow down the timeline.
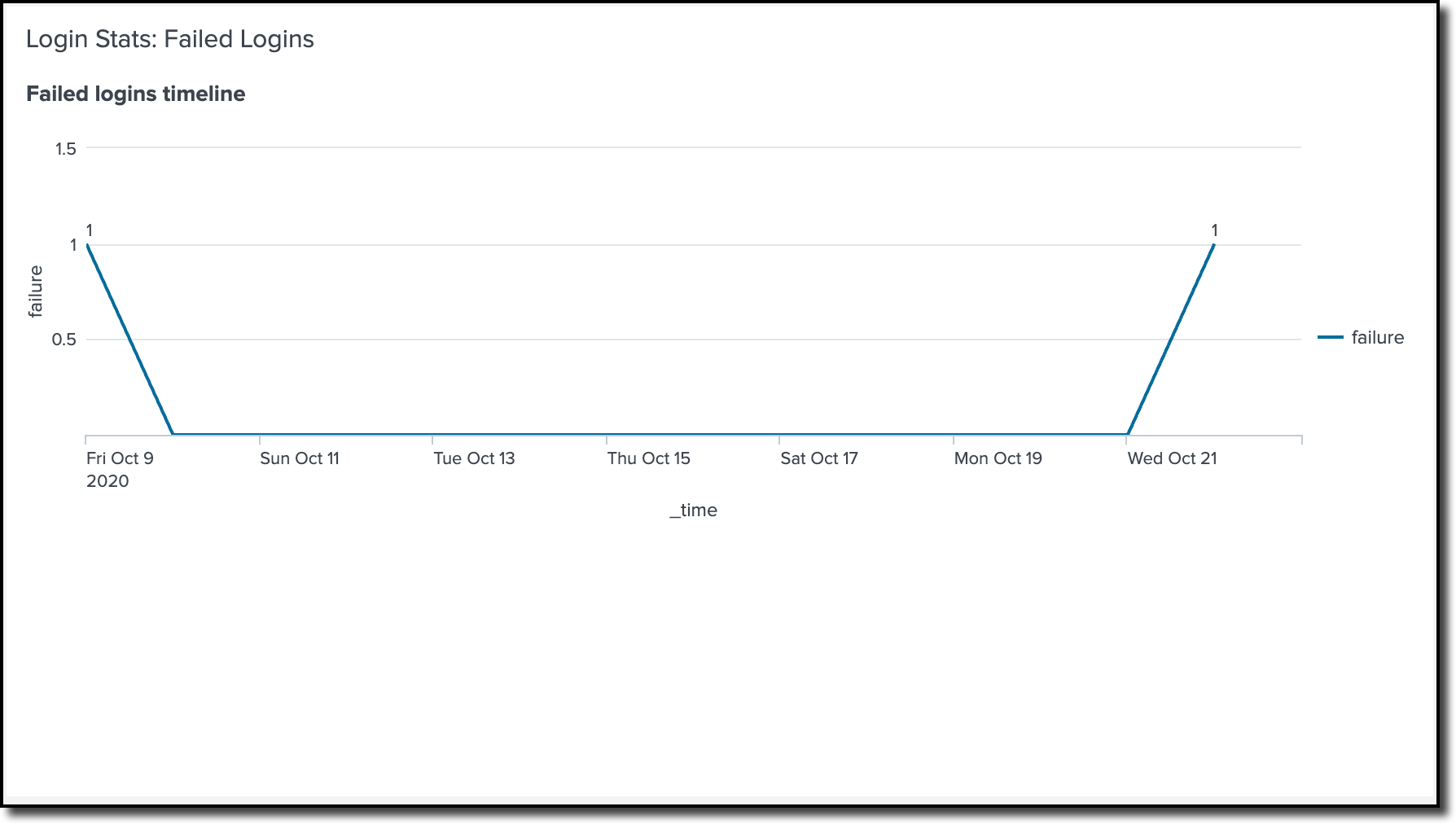
Figure 2: Failed logins time chart
2: Backups browsed
This view provides the Backup administrator if anyone has browsed through any historical backups, even if they have not performed a restore. This event is critical to track because it will track if anyone has browsed the CEO’s emails in the backup or browsed Payroll information in the backup. This view has drill-down enabled; once clicked on particular data, it will provide detailed information on which entity was browsed in specific and when it was browsed.
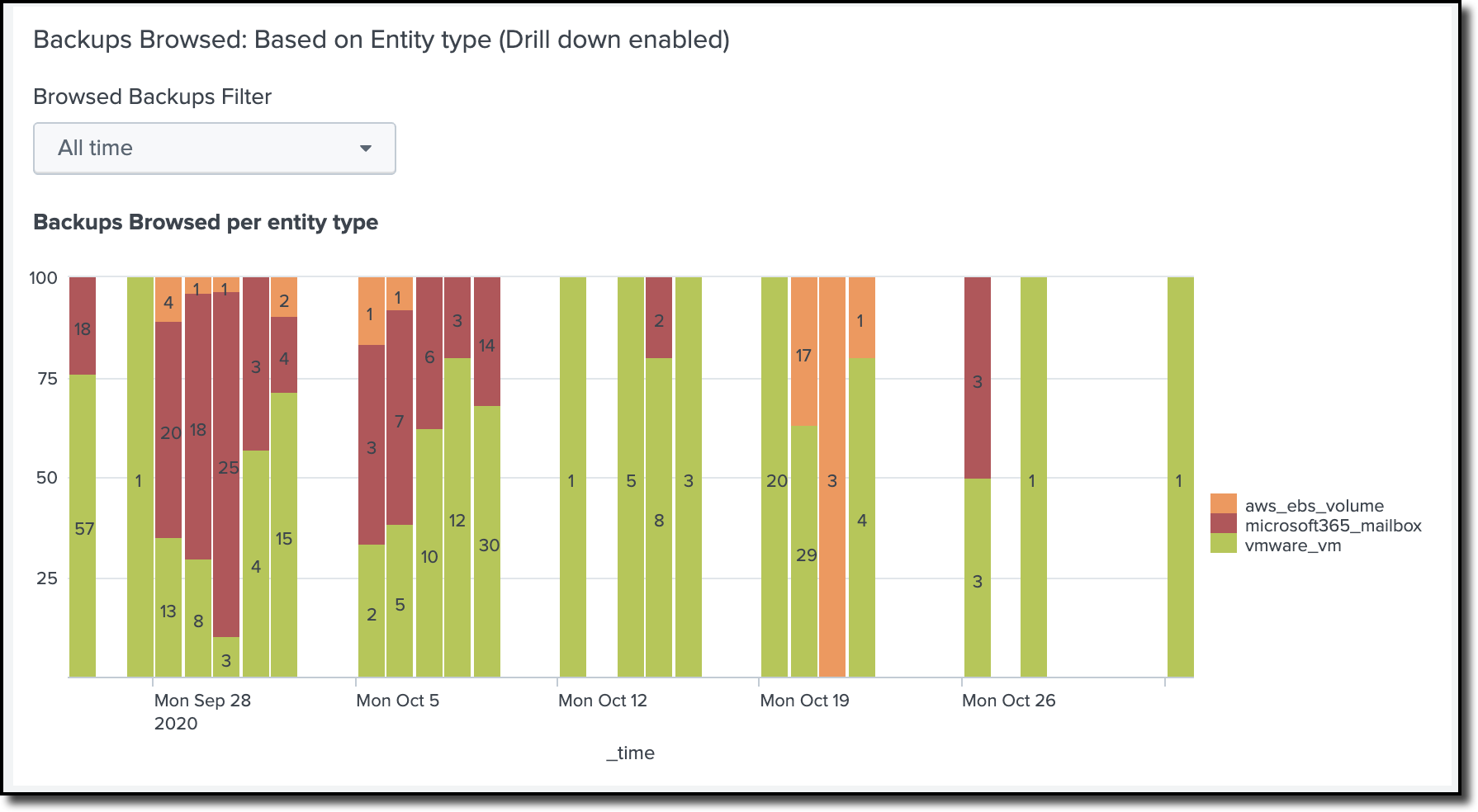
Figure 3: Backup browsed view
3: Datasources Stats
The view equips the Backup administrator with all the changes (Register, Update, Remove) made for data sources. Clumio can be configured to protect the following data sources, Amazon Elastic Block Store (EBS) volumes, Amazon Relational Database Service (RDS) resources, Microsoft 365 Exchange Online mailboxes, VMware vSphere virtual machines, etc. The record must have the details about the user making the change and the time the change was made. This view has drill-down enabled; once clicked on particular data, it will provide detailed information on which entity was browsed in specific and when it was browsed.
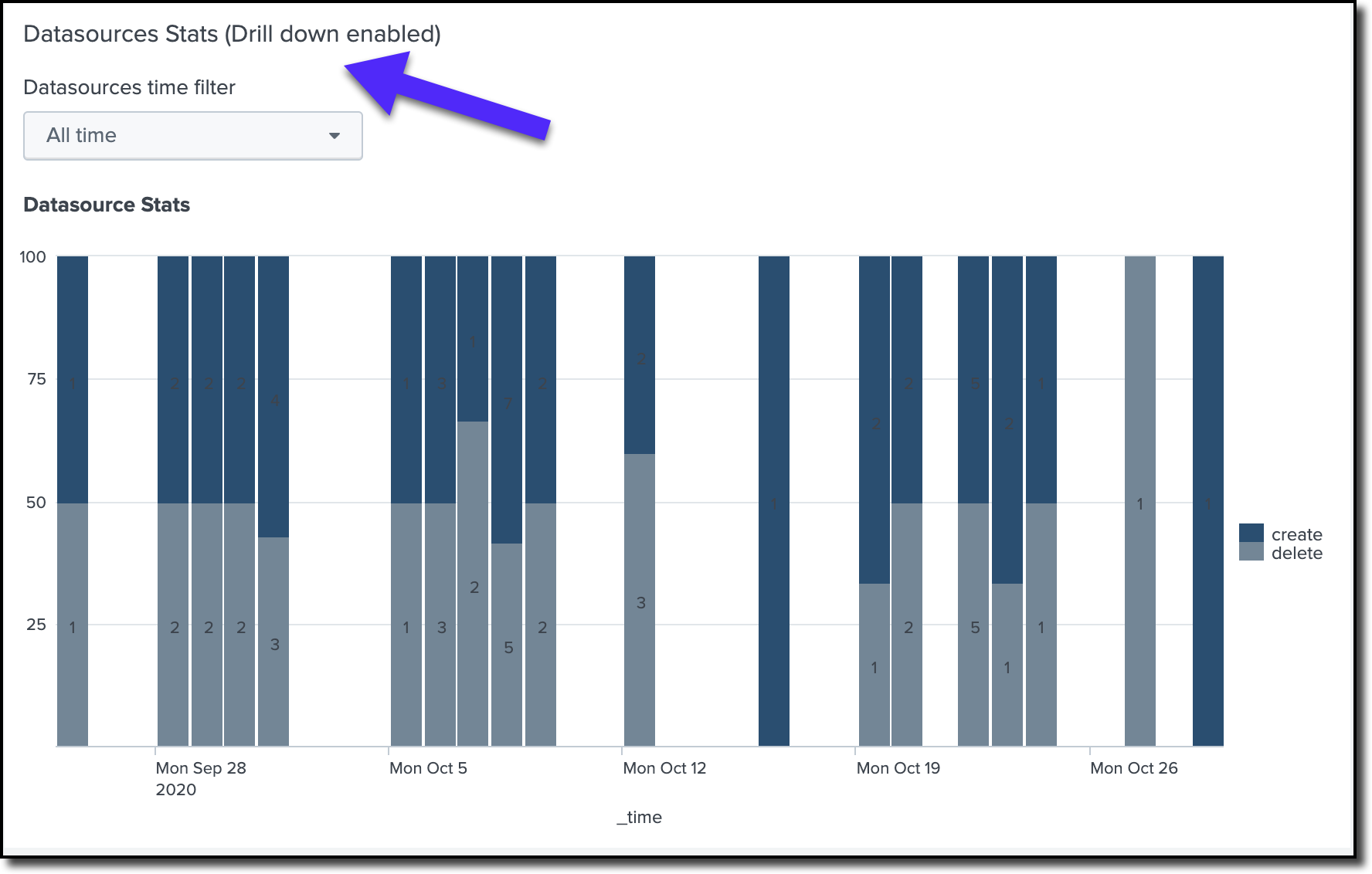
Figure 4: Datasource stats
There are many more visualizations in the Clumio Splunk app. All provide insightful information into restores and backup searches etc. This Clumio app is the first version of the app. So, please let us know your feedback and keep enriching the app with more dashboards and views.
Happy Splunking, and stay safe. Keep healthy !!!
