Commvault Unveils Clumio Backtrack - Near Instant Dataset Recovery in S3
Introducing Clumio’s integration with AWS CloudTrail Lake
Audit logs are a vital tool in any security team’s toolbox. They help track and monitor user activity across applications, systems, and networks.
Not only do they help identify suspicious activity, like a user accessing a privileged system they don’t have access to, but also are a key piece in forensically looking at the history and timelines of an event to determine everything that happened.
Audit logs don’t only help when it comes to bad actors but also just simple human accidents. If a production deployment fails or an application outage occurs, audit logs can still be leveraged to recreate the events, identifying a breakdown in process or procedure and allowing teams to avoid similar complications in the future.
The challenge with audit logs today
One major challenge customers face with audit logs is that they’re not aggregated in a central location that is fully immutable. SaaS applications specifically tend to have their audit logs kept within the SaaS application itself, oftentimes with only a 90-day history.
This leads to complicated scripting or the periodic export of logs from each application to place in a centralized location to meet corporate compliance and security goals.
This is a heavy lift on IT departments, and with hundreds of applications under management in any environment, it’s oftentimes not feasible to accomplish this completely.
Consolidating audit logs with AWS CloudTrail Lake
With the release of CloudTrail Lake, AWS has made it simpler to manage audit logs from disparate sources. CloudTrail Lake is a managed security and audit data lake that lets organizations aggregate, immutably store, and query events recorded by AWS CloudTrail.
This can be done across different regions and accounts – and is backed by a 7-year default retention policy to help you meet compliance requirements.
Customers can ingest and analyze events in an AWS CloudTrail compatible schema from Clumio, as well as other third-party and non-AWS sources to streamline auditing, security investigation, and operational troubleshooting.
Simpler data security with Clumio and AWS CloudTrail Lake
AWS and Clumio teamed to deliver this integration for CloudTrail Lake that allows you to simplify and streamline the process of consolidating activity data.
Through the newly launched PutAuditEvents API for AWS CloudTrail Lake, Clumio has created a simple integration to capture user activity information and events from your Clumio environment alongside the AWS systems you are protecting with Clumio.
Once the integration is enabled, you’ll be able to capture and store audit activity across various categories. This will allow you to easily answer many security and compliance-related questions across various categories such as:
- Authentication – Was there a high volume of unsuccessful logins to the Clumio console, indicating a brute force entry attempt or an issue with your Single Sign On provider?
- User Management – When was a user added to the Development Organization in Clumio, and when were they given the backup Admin role?
- Backups – When was a backup policy accidentally changed? This will help you quickly determine when a backup policy was changed or created to ensure you’re always meeting both long-term compliance requirements and maintaining any minimum required RPO’s (recovery point objectives).
- Restores – Is someone browsing the CEO’s email history, or trying to recover Payroll information from a system backup? This activity is tracked even if a restore hasn’t been initiated.
- S3 Protection Groups – When was a new S3 production bucket added to a protection group? Why was a bucket removed?
Setup and Architecture of Clumio logs on AWS CloudTrail Lake
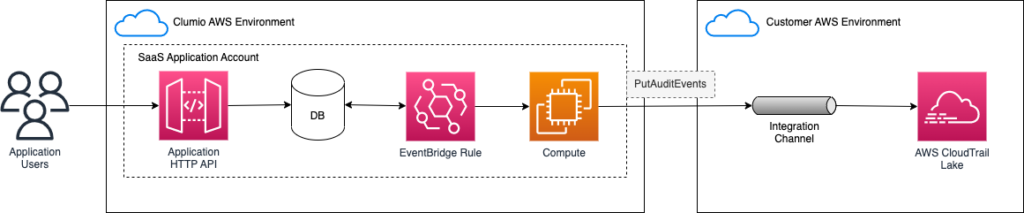
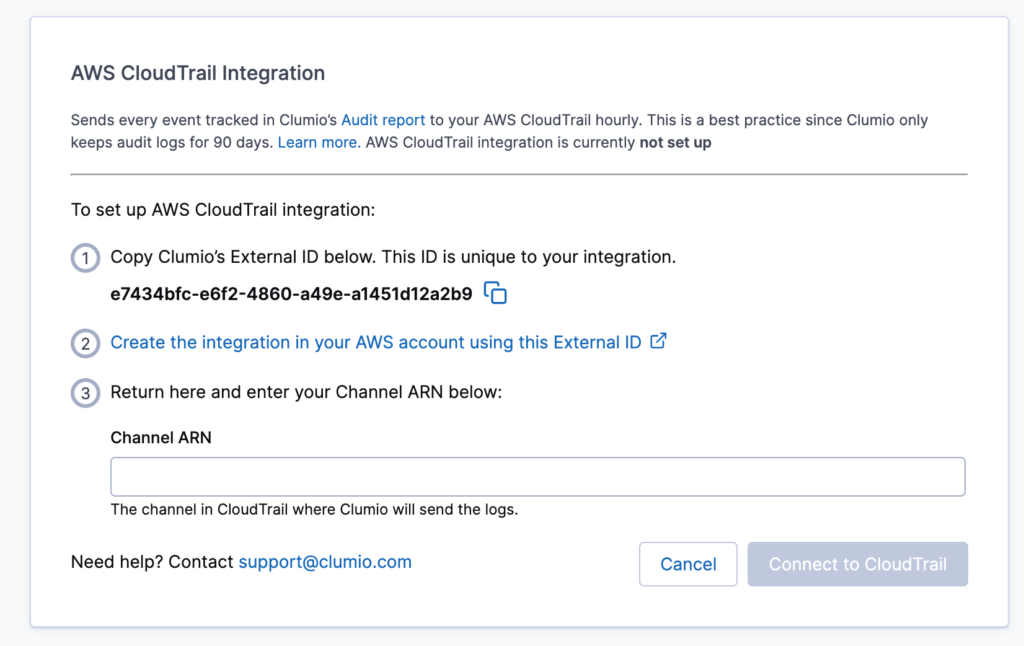
First, in Clumio, navigate directly to the Audit Report page. You’ll see a link to set up the integration in the upper right corner. You must have the Super Admin role to set up the integration.
AWS CloudTrail Integration

On the next screen, you will see an external ID unique to your integration with CloudTrail. Copy this value, and we will then setup the next portion of the integration in AWS directly.
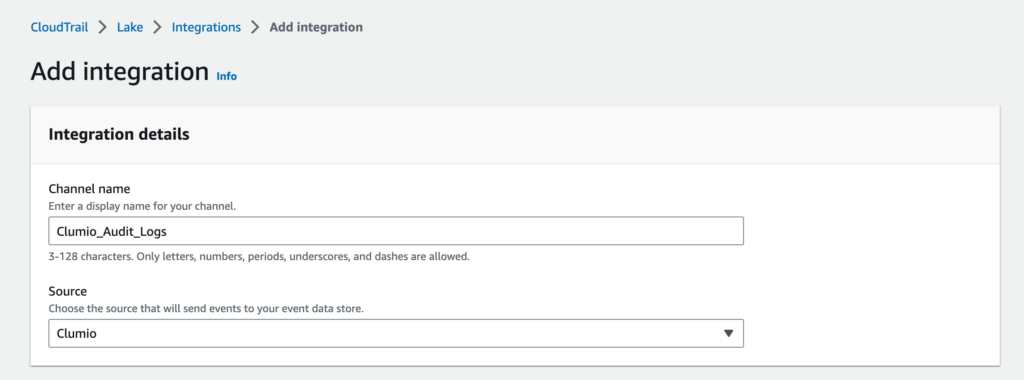
After logging into the AWS Console, navigate to CloudTrail, where you will find a new Integrations section under Lake. Click on the Add Integration button to configure the Clumio integration.
You’ll first need to give a name to channel that Clumio will use to send the audit logs data through, and then select Clumio as the source.
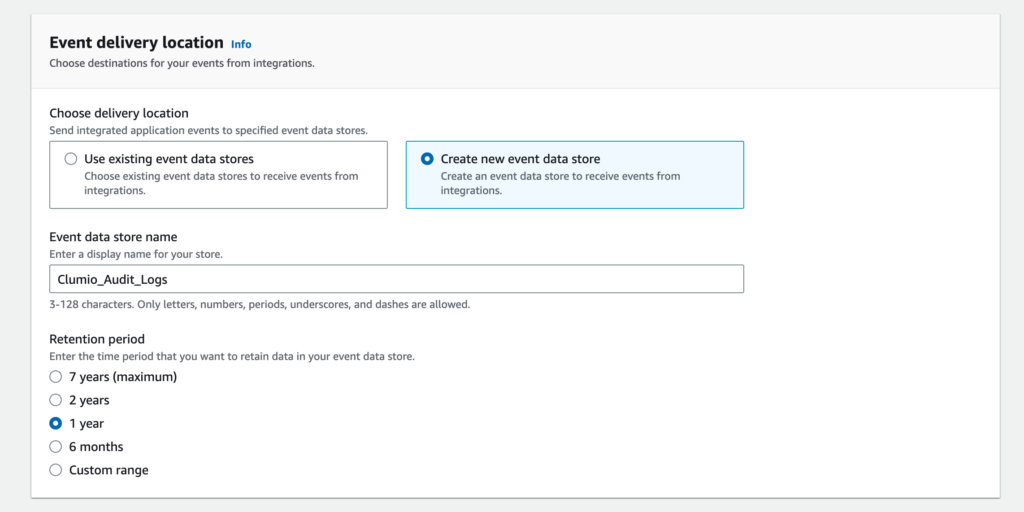
Next, we will need a place to deliver the Clumio audit logs and determine how long you would like to get the logs. You can either use an existing event data store or create a new one for this integration.
Next, we’ll configure the resource policy which is what will provide Clumio with a secure way to send the audit log data across the channel. This is where we will paste in the external ID we copied from the Clumio interface.
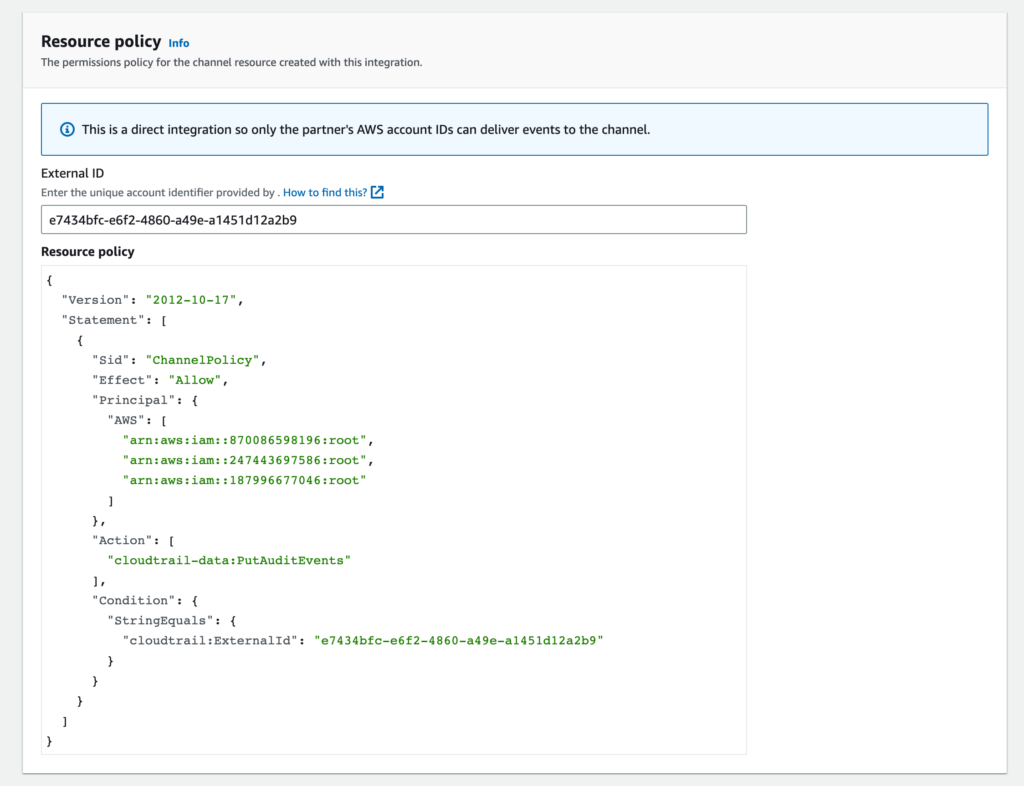
Lastly, apply any tags you may want to add to the resource and select Add Integration.
The integration is now set up; however, we have one final step. We need to copy the Channel ARN value and bring it back to Clumio, so we can complete the setup.
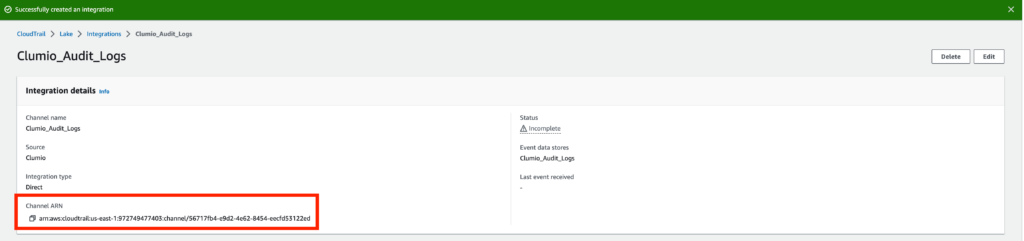
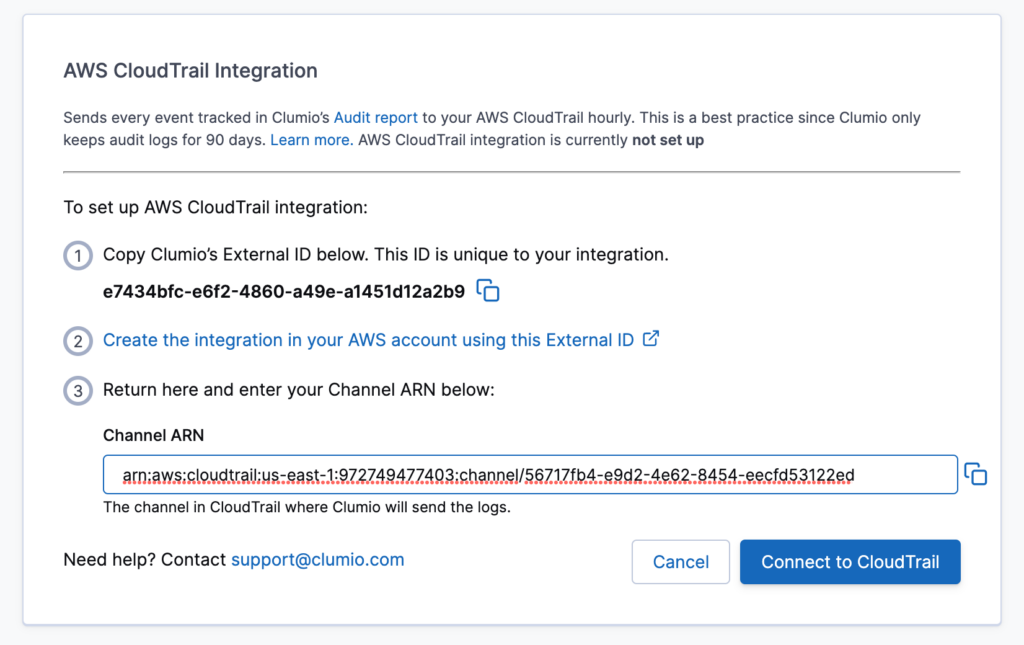
Once you add the Channel ARN value, click on Connect to CloudTrail.
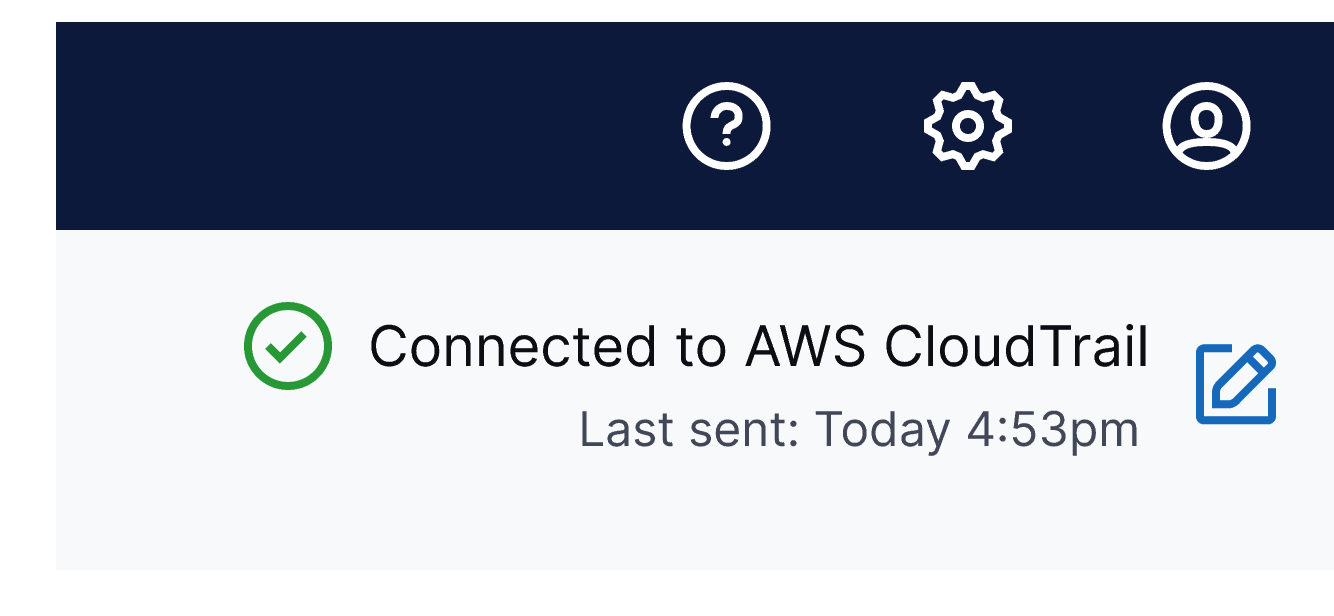
An initial event will be sent to the CloudTrail Lake event data store, allowing you to verify connectivity. From there, your Clumio audit events will be regularly sent to the CloudTrail Lake data store.
Additionally, you’ll be able to monitor the health of the integration at any time through the Audit Log report.
Below is a list of all audit event categories that are sent to CloudTrail as part of this integration:
- Authentication
- Datasource
- Policy
- S3 Protection
- Restore
- Backup
- Users
- Organizational Unit
- KMS Config
- SSO/MFA
- CloudFormation template
This new integration is available for all customers. If you’re interested in using CloudTrails with Clumio, please follow our detailed setup instructions or contact support@clumio.com.
